Hijacking a phishing campaign: Beating cybercriminals at their own game
Bypassing e-mail security filters using unregistered domains
Over the past months, I’ve noticed a strange phenomenon that kept popping up in phishing campaigns. Cybercriminals have been sending out phishing emails that contain links to URLs hosted on domains that are not (yet) registered.
This peculiar tactic piqued my curiosity, and I decided to investigate further. For this, I used the following real life example (send out on the 6th of January 2025) as a starting point:
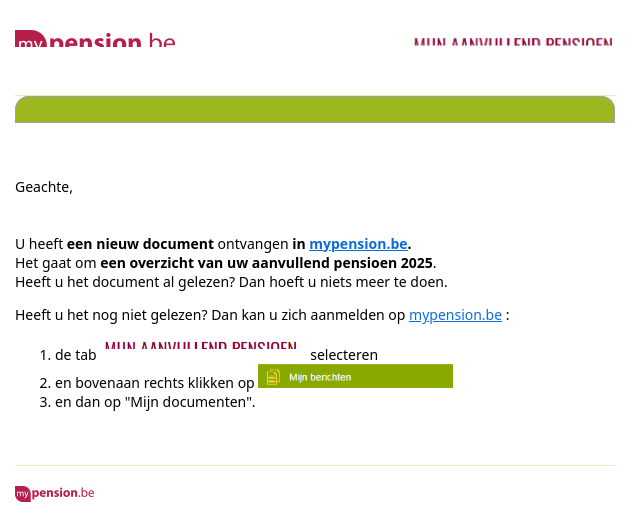
In this case the attackers pretended to deliver official communication from Belgium's online pension portal mypension.be.
But as you might have expected, the URL in the e-mail was not pointing to the official website. Instead, the URL hidden behind was: https://uhiwedfnewdi[.]com. Normally this would lead to a phishing website, but in this case the domain was not registered yet.
Why Would Attackers Use Unregistered Domains?
While it’s difficult to pinpoint the exact reasons behind this approach, there are a few potential explanations:
-
Bypassing Spam Filters
Many antivirus solutions and email security filters rely on URL reputation systems to detect malicious links. These systems check domains against blacklists and analyze metadata such as the date of registration. However, an unregistered domain has no history, making it nearly invisible to such checks.Attackers can send phishing emails containing these URLs and register the domain only after the emails have arrived in people's inboxes. This allows them to evade early detection and maximize the impact of their campaign.
This with the caveat that they will probably miss the first wave of victims, as the domain is not yet registered.
-
Other more boring explanations
Some automated systems that generate phishing domains may be prematurely sending out emails before the domain registration is complete. This could be a bug in the attackers’ infrastructure.It’s also possible that this is simply a typo or a human oversight in the attacker's setup, where they mistakenly include a domain they haven't yet registered.
Both of these explanations seem less likely to me, as the attackers have been using this tactic for a while now.
Turning the Tables
As I continued my investigation, I couldn’t resist: I decided to register one of these domains before the attackers could. In essence, hijacking their phishing campaign.
I quickly set up a warning page and enabled logging and analytics to observe what would happen next. The results were quite interesting.
Key Insights from the Captured Campaign
-
- Visitors:
-
The website received approximately 2,000 unique visitors (excluding bots), from within Belgium. This was the most shocking part of the data for me. Of course I can't be sure if all of these visitors were potential victims who would have filled in their personal details, bank information or passwords, but it's still a concerning number.
-
Referers:
-
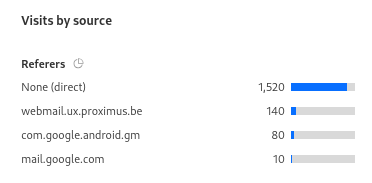
Based on the referer headers, I found that:
- 160 visitors clicked the link from the Proximus webmail application.
- 100 visitors accessed it through Gmail.
-
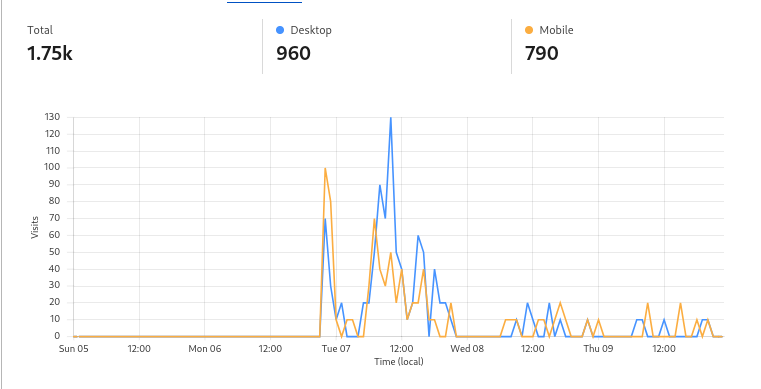
Devices:
- Immediately after registration, most visits came from mobile devices.
- The next morning, the majority of visits came from desktops and laptops.
-
Browsers:
- Edge was the most used browser, followed by the mobile versions of Chrome and Safari.

- Edge was the most used browser, followed by the mobile versions of Chrome and Safari.
What Does This Mean?
The fact that a phishing campaign can bypass spam filters using unregistered domains is quite concerning, but defending against this isn't as easy as it seems.
Registering domains that appear in suspicious emails is not a scalable solution, neither is blocking all e-mails containing unregistered domains. However, it’s crucial to be aware of these tactics and adapt your security measures accordingly.
Monitoring for unregistered domains and sending alerts to security teams for an additional check, or monitoring urls/domains for when they become active and immediately taking action could be a viable approach.
Final Thoughts
This was by no means thorough research, and I still have a lot of questions, but I'm very curious to hear other people's thoughts on this topic. Have you encountered similar tactics in phishing campaigns? How would you recommend addressing this issue? Feel free to reach out to me on LinkedIn or via e-mail: jeroen.gui@justguard.be
Stay safe and vigilant!
PS While the domain uhiwedfnewdi.info is now in my possession, I monitored for any suspicious activity, trying to circumvent my hijacking, and found uhiwedfnewdi1.info, registered about 2 hours after my intervention. A couple of pivots later about 10 website takedowns were initiated. But that's a story for another time...
